
The Right Way to AI
When deploying AI, a little planning goes a long way. Here’s some advice from @Microsoft on steps you can take to a successful #AI adoption – which includes getting employees to embrace it. Read the article. 👀

When deploying AI, a little planning goes a long way. Here’s some advice from @Microsoft on steps you can take to a successful #AI adoption – which includes getting employees to embrace it. Read the article. 👀

When running a small or medium-sized business (SMB), security should never be an afterthought. With cyberattacks becoming more advanced, having reliable antivirus software is one

Ready to take your business’s VoIP (Voice over Internet Protocol) experience to the next level? Enter 5G — a technology that’s redefining how we connect
The crush of data, information, meetings, and always-on communications makes it harder for people to focus on important work. Read how #AI can free up more of your time in this @Microsoft article.

Looking to streamline your IT operations with a single ecosystem? Microsoft Windows 11 Pro PCs can make it happen. With Microsoft services and applications like App Assure and Test Base10 for Microsoft 365, Autopilot and Fast Track your IT team can plan, assess, manage and deploy your next migration to the latest versions of Windows 11 with 99.7% application compatibility. DM us when you are ready to get your next migration off to a seamlessly successful start.

When the Alabama Appellate Court System needed to overhaul and upgrade its outdated but still functional IT infrastructure, they called on @Microsoft to digitize justice systems and accelerate secure and transparent proceedings. By migrating many of its on-premises operations to a more secure cloud environment on Microsoft Azure, justices, employees, and 6,000 outside attorneys benefit from remote access, more efficient operations, and improved security. DM to discuss upgrading your firm’s IT infrastructure with MS Security and Azure Cloud.

Check out this customer story for a first-hand account of how Windows 11 Pro devices help Calgary Sports focus on five teams, two stadiums, and thousands of fans—while staying secure and productive in everything they do, from broadcast systems to in-game feeds to business operations. DM us for details on how to get started with Windows 11 Pro.
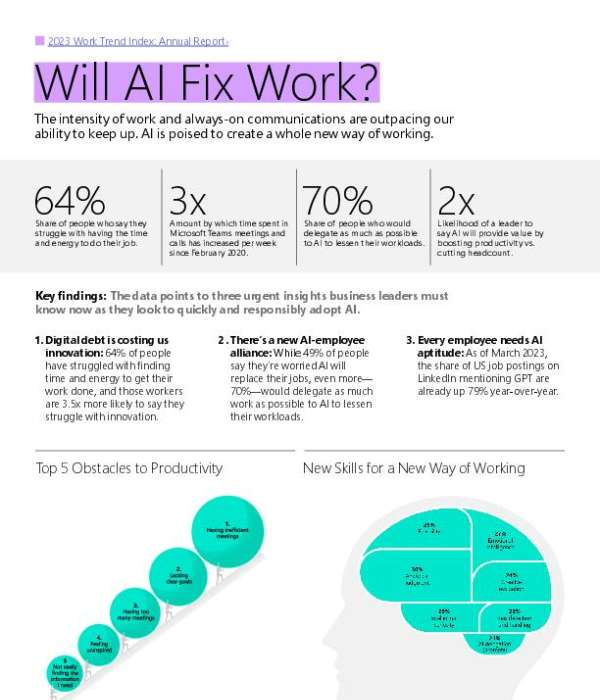
68% of people say they don’t have enough uninterrupted focus time during the workday. View this infographic to learn how @Microsoft Copilot can help you get more done by serving as every employee’s personal #AI assistant. @msftcopilot
Managing your emails doesn’t need to be overwhelming. With Outlook in Microsoft 365, you can effortlessly organize your inbox, simplify scheduling, and communicate more efficiently

Business intelligence (BI) is revolutionizing the way companies operate, specifically by providing deep insights that drive efficiency and growth. Businesses across different industries leverage BI


